Credentials
If you would like to import from your Cloud or deploy infrastructure from Opsly, then you need to configure credentials to connect to your Cloud accounts. Opsly uses Vault to store your access keys in a secured vault which are never seen, exposed and used. Instead whenever you import or deploy, Vault generates temporary access keys which only live until the import/deployment is finished.
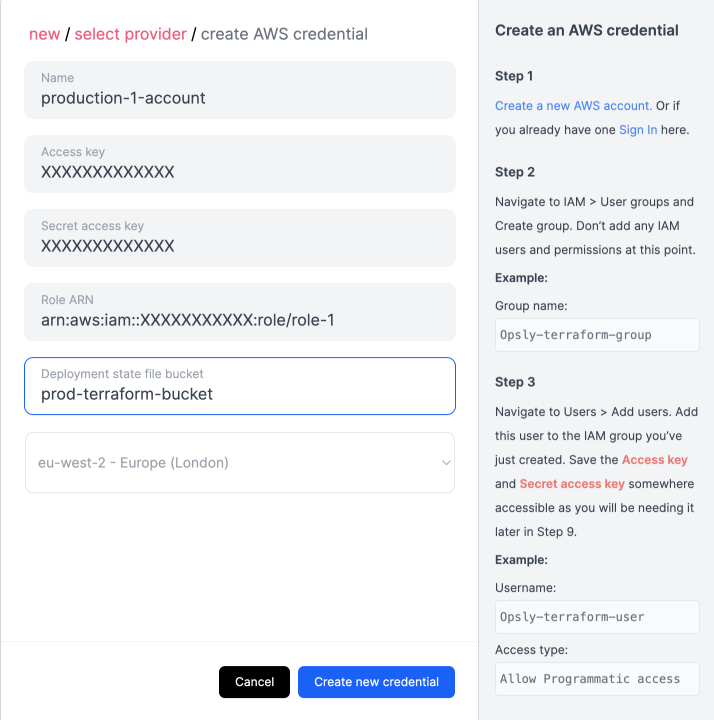
Create AWS Credential
To create an AWS credential, you need to create the following IAM resources first in your AWS account so Opsly can access and deploy to your AWS account securely. Each credential is tied to an IAM role so you can have multiple credentials (different IAM roles) connecting to the same AWS account.
- An IAM user with with a policy that executes
sts:AssumeRole - An IAM role with a policy granting the relevant permissions for Opsly to deploy resources into your AWS account
You can find a step-by-step guide on the IAM resources you need to create in the Dashboard. New > Credentials > AWS.
Once you have created the resources
- Copy the access key and secret key of the IAM user
- Copy the role ARN
- Specify the name of an existing S3 bucket where Opsly will store the Terraform state file
- Select a region where the S3 bucket is located
Create Microsoft Azure Credential
To create an Azure credential, follow the steps below to create the relevant ids and secret keys that Opsly will use to connect to your Azure account.
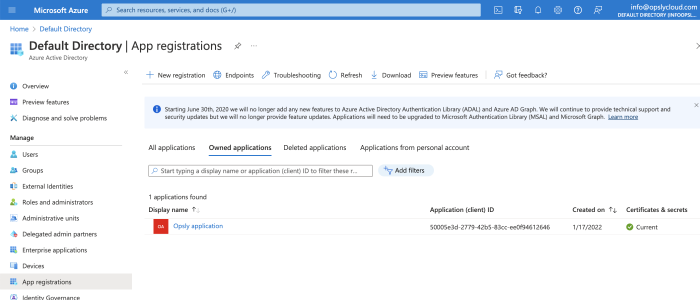
- Register a new app (Azure Active Directory > App Registrations > New registration)
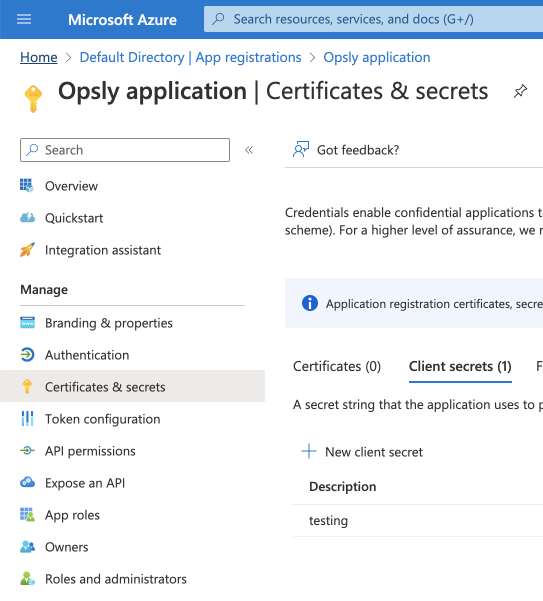
- Create a secret key (Click on the app > Certificates & secrets > New client secret > Decide upon an appropriate expiry/rotation date). Save this for later
- Ensure all the API permissions are added (API permissions > Add a permission)
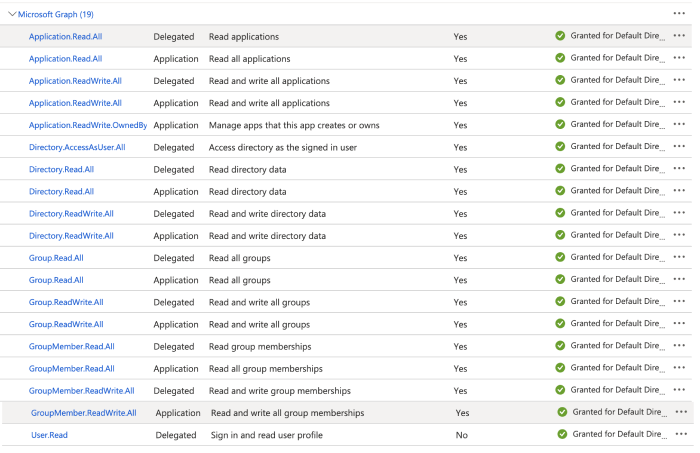
- Assign your application to a user/role (Azure Active Directory > App Registrations > Overview > Go to Enterprise applications > Assign users and groups / Roles and administrators). Grant the appropriate permissions to a user/role based on what Opsly needs to deploy resources into your Azure account.
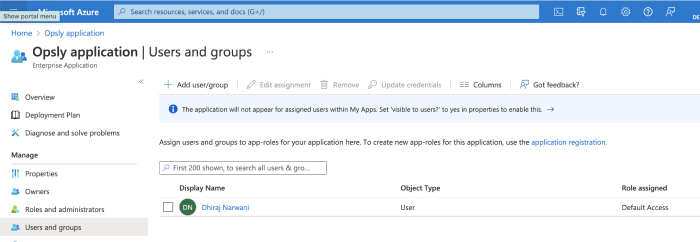
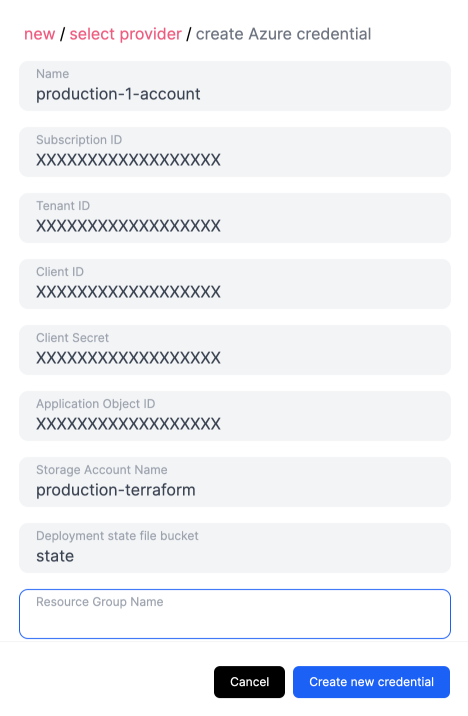
Once those resources are created
- Copy the Subscription ID (Home > Subscriptions)
- Copy the Tenant (directory) ID (Azure Active Directory > App registrations)
- Copy the Client (application) ID (Azure Active Directory > App registrations)
- Copy the Client secret created previously
- Copy the Object ID (Azure Active Directory > Enterprise Applications)
- Specify the name of an existing Storage Account
- Specify the name of a container in an existing Storage account where Opsly will store the Terraform state file
- Specify the resource group where the existing storage account exists (optional)
Create Google Cloud Platform credential
To create a GCP credential, you need to create a Service account and grant it the relevant permissions for Opsly to deploy resources.
Go to your GCP account > IAM & Admin > Service accounts > Create service account.
Give it a name and grant the relevant permissions what Opsly needs to deploy resources into the account. You can create custom roles or use managed roles. You can also grant users access. You must grant the below permission
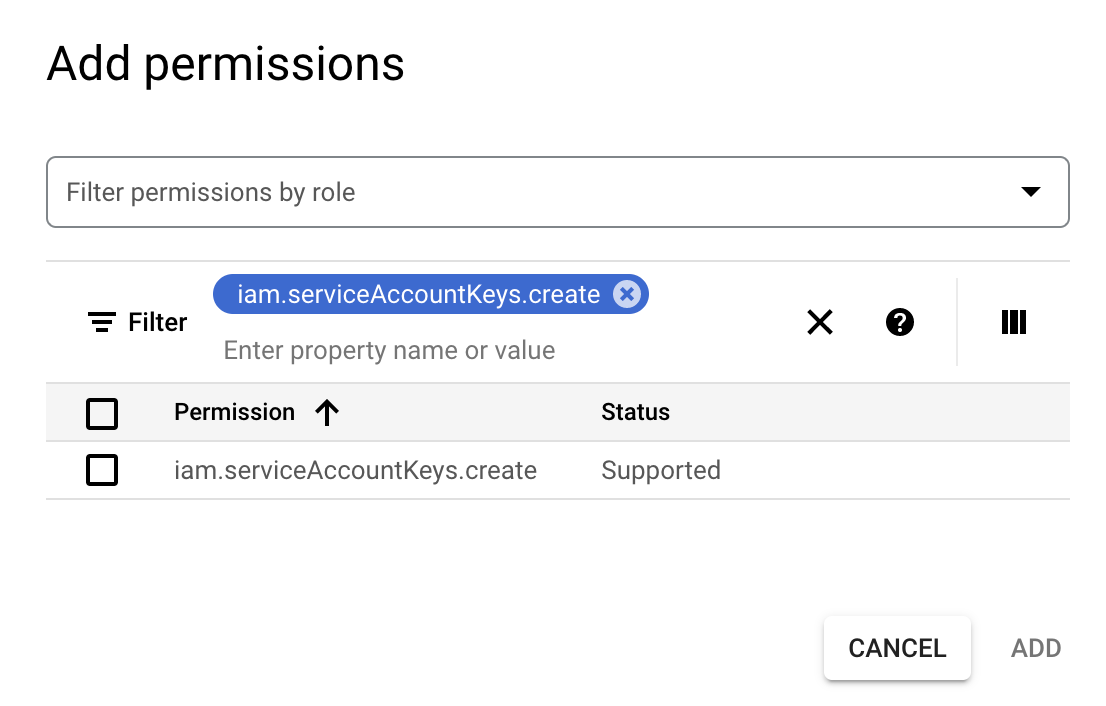
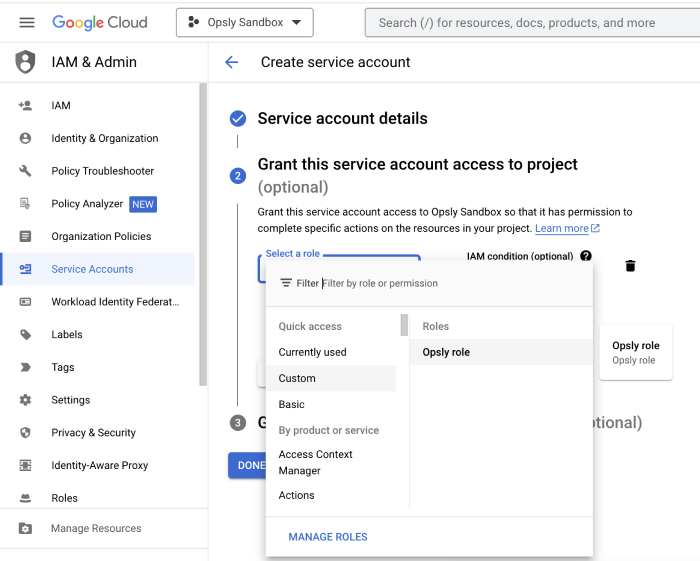
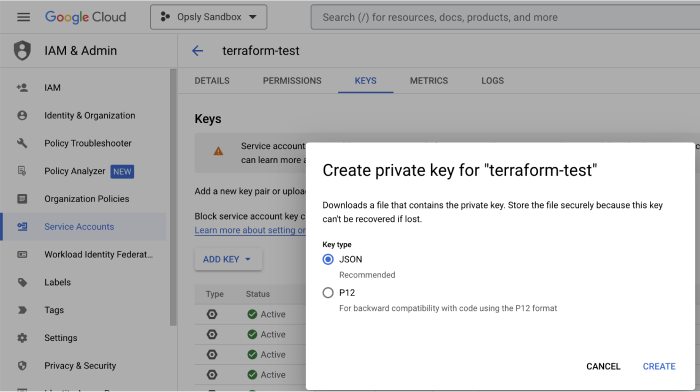
- Select the service account you've just created > Keys > Add Key > Create new key. This will download a JSON file with the private key. Save this for the next step.
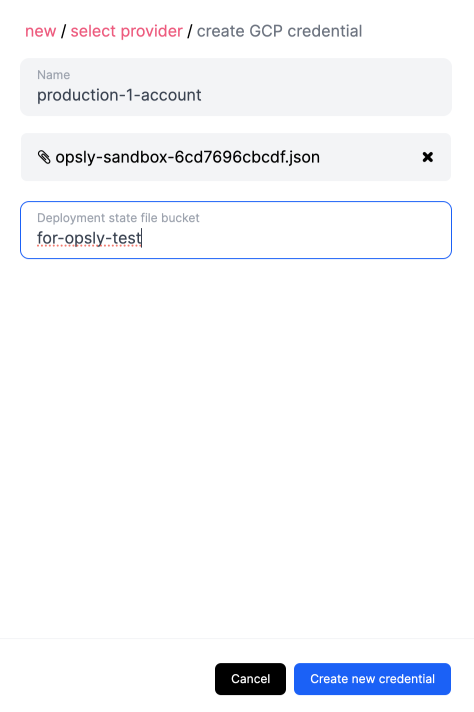
- Go back to Opsly and upload the downloaded JSON file. This will get stored in the Vault securely. Specify the name of an existing Cloud Storage bucket to store the Terraform state file.
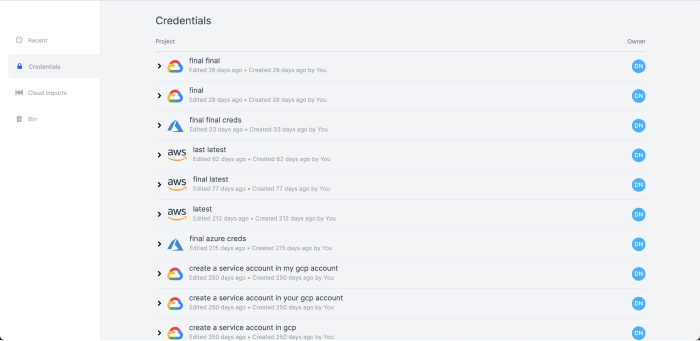
Update and delete credentials
All your Multi-cloud credentials can be found in the Credentials page (select Credentials in the Dashboard on the left-hand side).
You can select a credential and update its name or description. You cannot update any of the other fields - if you want to change anything else you need to create a new credential.
You can also delete credentials and this will permanently be deleted from the Vault.