Export Terraform Code
You can export Terraform code from a diagram instead of using Opsly to deploy to your Cloud. This is ideal if you are using your own CI/CD or you don't want to insert your Cloud credentials.
Ensure the toggle Export code is enabled on a diagram - this can be updated from the Dashboard.
In the diagram page at the top right hand-side you will see an Export code button. Click that and it will download a zip of the entire Terraform code repository. You can push this to GitHub and run this in your CI/CD processes with your own credentials.
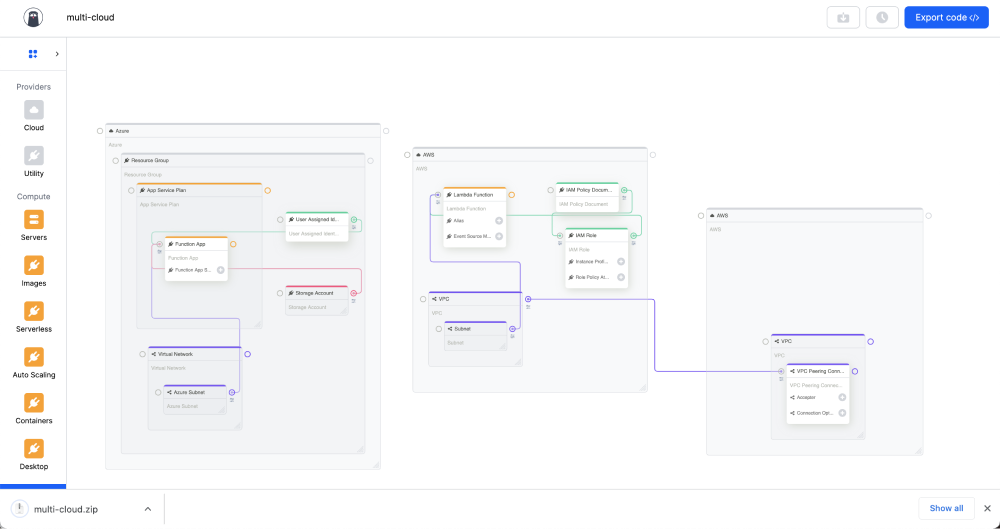
Terraform structure
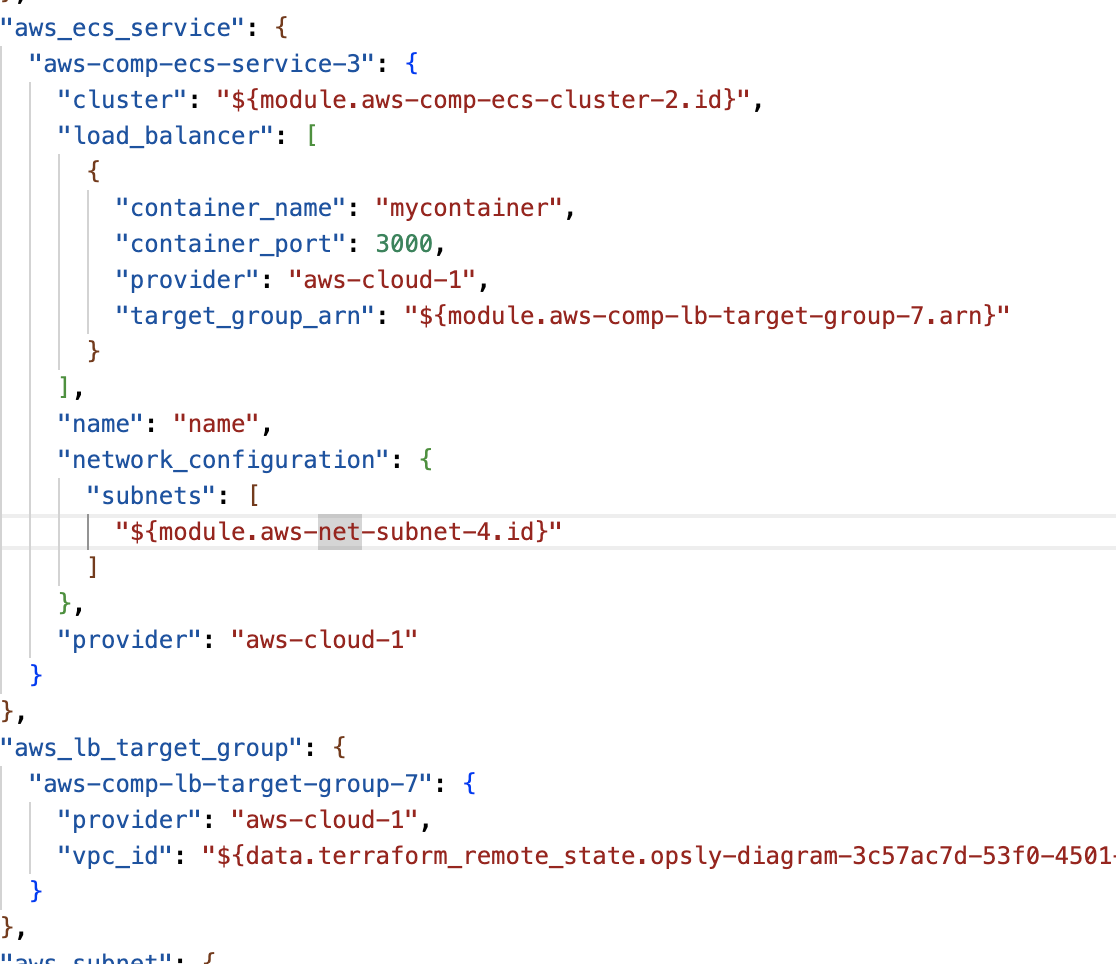
If you unzip the downloaded file, you will see the generated Terraform code.
We don't use any pre-made Terraform code or any framework we have developed. We follow all Terraform best-practices and generate a full repository of Terraform line-by-line generated code.
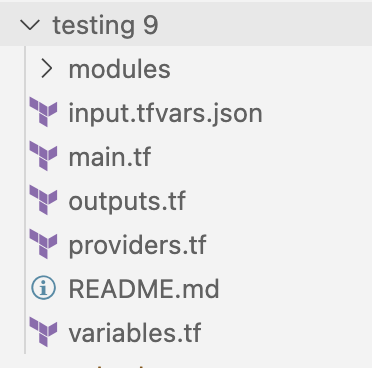
All resources are generated in modules/. These modules are referenced in the main.tf using source. You can also have custom modules coming from your own Git sources. We use terraform_remote_state to reference resources imported or deployed in your Cloud. All references between modules are generated automatically and these don't need to be touched.
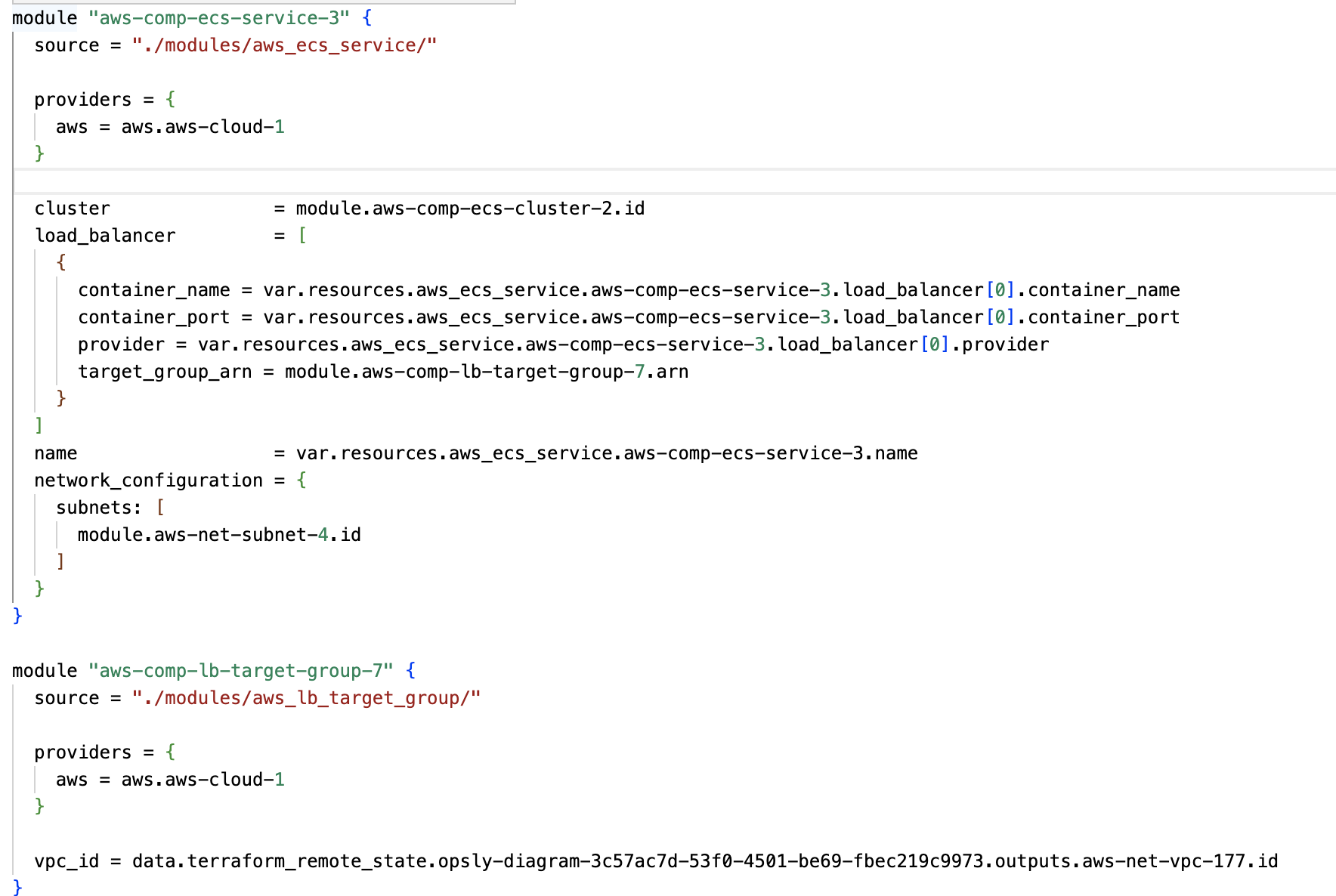
We generate a .tfvars.json file with all the configuration values. This is ideal as it works nicely if you have multiple .tfvars (1 per environment) keeping the same main.tf Terraform infratructure deployed across multiple environments.
How to run Terraform code
To build and deploy modules, first run:
terraform init to initialise Terraform
To build
terraform plan -var-file=input.tfvars.json and it will prompt you to input your access keys from variables.tf.
Alternatively you can pass the keys as inline variables.
terraform plan -var-file=input.tfvars.json -var=aws-cloud-1_access_key=XXXXXXX -var=....
When you are ready to deploy swap plan with apply
terraform apply -var-file=input.tfvars.json -var=aws-cloud-1_access_key=XXXXXXX -var=....
Custom modules
When using modules from your own Git sources, the main.tf might not contain the provider blocks as you will be using your own provider versions. You should create the provider blocks and alias in the modules where necessary in the main.tf and pass your access and secret keys.
Alternatively you can override the access and secret keys from your own provider block variables declared in the source repository:
terraform plan -var-file=input.tfvars.json -var=resources.terraformstaticwebsitescloudfront.cm__terraformstaticwebsitescloudfront-10.access_key_id=XXXXXXX -var=resources.terraformstaticwebsitescloudfront.cm__terraformstaticwebsitescloudfront-10.aws_secret_key=XXXXXX
Coming soon (CI/CD integration)
Downloading the ZIP file and pushing it to CI/CD manually could be a lot of steps for you to deploy the Terraform code in a repeatable manner. We are launching a CI/CD integration soon where in Opsly you can connect the CI/CD that you are using. In Opsly you can click Deploy and automatically it will send that code to the CI/CD and run the deployment process there. Please contact us here if you would like to learn more and how you can start using this feature.